Microsoft 365: How to Warn Users About MFA Bypass Attacks (AiTM Phishing)
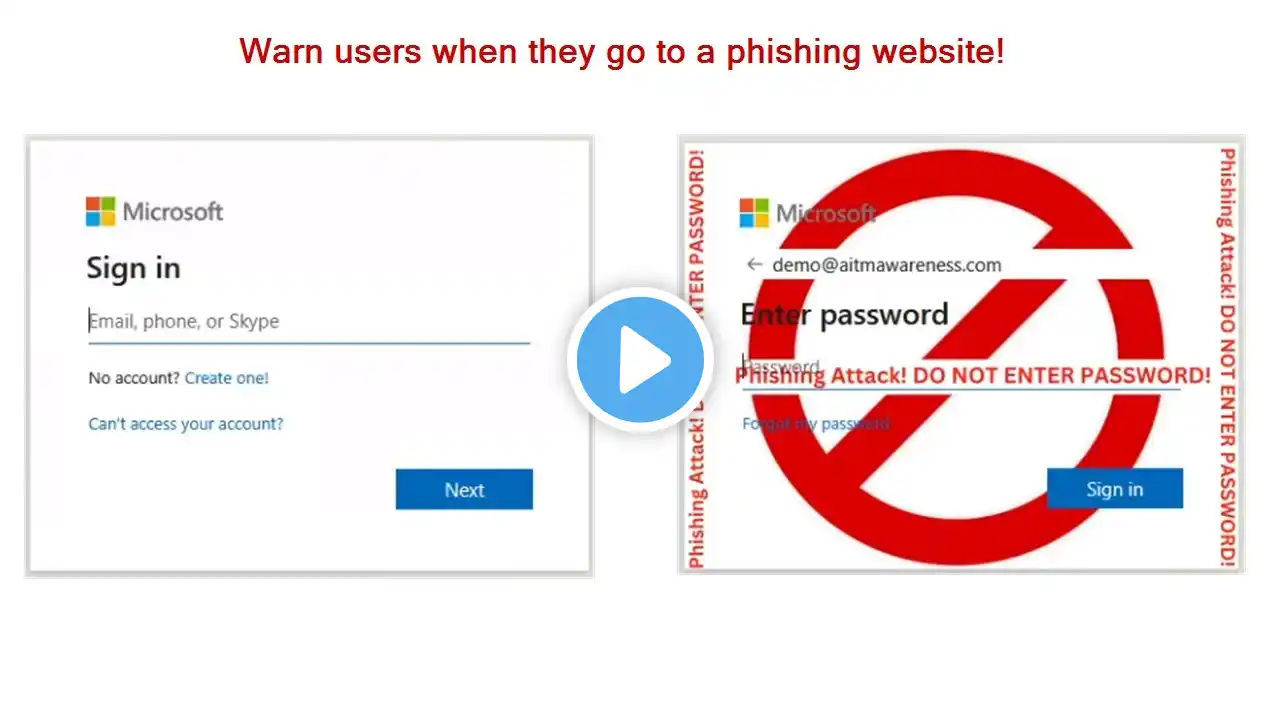
In this video, I demonstrate how attackers can bypass MFA in Microsoft 365 using Adversary-in-the-Middle (AiTM) phishing kits. These attacks proxy Microsoft's login page to steal user credentials and session cookies in real time—even when MFA is enforced. To help users detect and respond to these threats, I walk through a detection method that changes the background image on phishing login pages, warning users not to enter their credentials. This is achieved using an Azure Function and Microsoft Entra ID's Custom Branding feature. What you'll learn: How AiTM phishing attacks work (with a demo) Why MFA alone does not stop these attacks How to display a warning to users who go to direct-proxy AiTM phishing sites. Limitations of this method and common evasion techniques Practical recommendations for integrating this into a broader defense strategy Links and Resources: Original concept by Attic Security by Zolder: https://zolder.io/blog/using-honeytok... Hosted AiTM Detection from Zolder: https://atticsecurity.com/en/aitm/ GitHub Repository referenced in video (AiTM Detector): https://github.com/chaimblack/AiTMDet... How to Set Up Company Branding (CustomCSS): https://learn.microsoft.com/en-us/ent... Clarion by Matt Kiely: https://github.com/HuskyHacks/clarion Original LinkedIn post from Kelvin Tegalaar: https://www.linkedin.com/posts/kelvin... CIPP by Kelvin Tegalaar: https://cipp.app/ Chapters: 0:00 Introduction 1:26 How authentication works (with and without MFA) 5:04 How attackers can bypass MFA using Adversary-in-the-Middle (AiTM) 9:50 Demo using EvilGinx to bypass MFA 16:30 AiTM detector introduction 19:34 Using Custom CSS in a custom login using Company Branding 23:10 History of AiTM detector: Zolder 26:10 History of AiTM detector: Matt Kiely - Clarion 27:32 History of AiTM detector: Kelvin Tegelaar - CIPP 29:50 Open-source version of AiTM detector on GitHub 31:00 AiTM detector demo 34:05 Batman! 35:30 How effective is the AiTM detector? 35:52 Limitations of the AiTM detector 40:00 Final thoughts Learn more about AiTM attacks: https://aitmawareness.com/ Learn more about AiTM Detectors: https://aitmawareness.com/aitm-detectors

