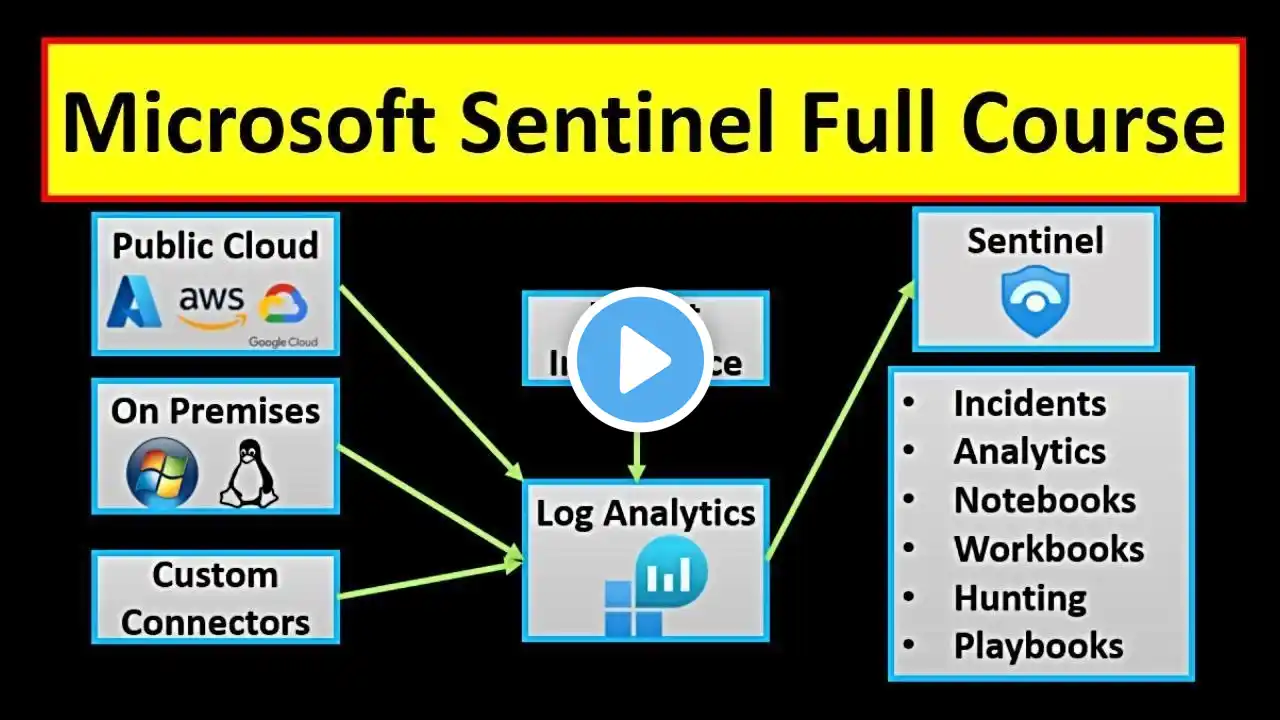
Microsoft Sentinel Training | Azure Sentinel Tutorial | Microsoft Sentinel Step-by-Step Guide
Welcome to CyberPlatter! I'm Navya, and in this full course, you’ll learn everything you need to know about Microsoft Sentinel (formerly Azure Sentinel). 👉 What you'll learn: Sentinel basics and architecture Key concepts explained in simple words Step-by-step demos How to start working with Microsoft Sentinel on your own Whether you're a beginner or just want to understand how Sentinel works, this course is perfect for you! 💻 No prior experience needed. ✅ By the end, you'll be confident using Microsoft Sentinel independently. 🔔 Don’t forget to like, subscribe, and turn on the bell icon for more cybersecurity content! Chapter 1: Microsoft Sentinel Architecture: • Microsoft Sentinel Tutorial: Introduction,... Chapter 2: Microsoft Sentinel Deployment and RBAC: • Microsoft Sentinel Tutorial: Microsoft Sen... Chapter 3: Microsoft Sentinel Content Hub and Data Connectors: • Microsoft Sentinel Tutorial: Microsoft Sen... Chapter 4: Connecting Entra ID to Microsoft Sentinel: • Microsoft Sentinel Tutorial: Entra ID inte... Chapter 5: Threat Detection and Mitigation Workflow in Microsoft Sentinel: • Microsoft Sentinel Tutorial: Threat Detect... Chapter 6 - Threat Intelligence in Microsoft Sentinel: • Microsoft Sentinel : Threat Intelligence |... Chapter 7: Microsoft Sentinel : Analytics Rules | Threat Detection: • Microsoft Sentinel : Analytics Rules | Thr... Chapter 8: Microsoft Sentinel User & Entity Behavior Analytics UEBA: • Microsoft Sentinel User & Entity Behavior ... Chapter 9: Ingest logs to Microsoft Sentinel using Azure Monitor Agent (AMA) : • Microsoft Sentinel |Ingest logs to Sentine... Chapter 10: Microsoft Sentinel Automated Responses: Automation Rules and Playbooks: Microsoft Sentinel SOAR Solution: • Microsoft Sentinel | Automated Responses t... Chapter 11: Microsoft Sentinel Workbooks | Data Visualization in Microsoft Sentinel: • Microsoft Sentinel Workbooks | Data Visual... Chapter 12: Microsoft Sentinel Watchlists: • Microsoft Sentinel Watchlists | How Micros... Chapter 13: Microsoft Sentinel Notebooks | How to Investigate Threats with Jupyter & MSTICPy: • Microsoft Sentinel Notebooks | How to Inve... Chapter 14: Microsoft Sentinel Incident Response: • Microsoft Sentinel Incident Response: How ... Chapter 15: Threat Hunting in Microsoft Sentinel | KQL, Hunting Queries & Live Demos: • Threat Hunting in Microsoft Sentinel | KQL... SIEM Interview Questions and Answers Part 1 - • SIEM Interview Questions and Answers | Par... SIEM Interview Questions and Answers Part 2 - • SIEM Interview Questions and Answers | Par... #cyberplatter #cybersecurity #security #securityconcepts #SIEM #SOAR #securitytools #securitytraining #cybersecuritytraining #securitytutorial #cybersecuritytutorial #cybersecsec #cybersecurityexperts #cybersecurityforbeginners #azure #microsoftsecurity #microsoftsentinel #microsoft #azuresecurity #azuresentinel Microsoft Sentinel Training Microsoft Sentinel Tutorial Microsoft Sentinel Full Course Azure Sentinel Training Azure Sentinel Tutorial Azure Sentinel Full Course How to set up Microsoft Sentinel


















