Man-in-the-Middle Attack via ARP Spoofing: A GNS3 Demonstration
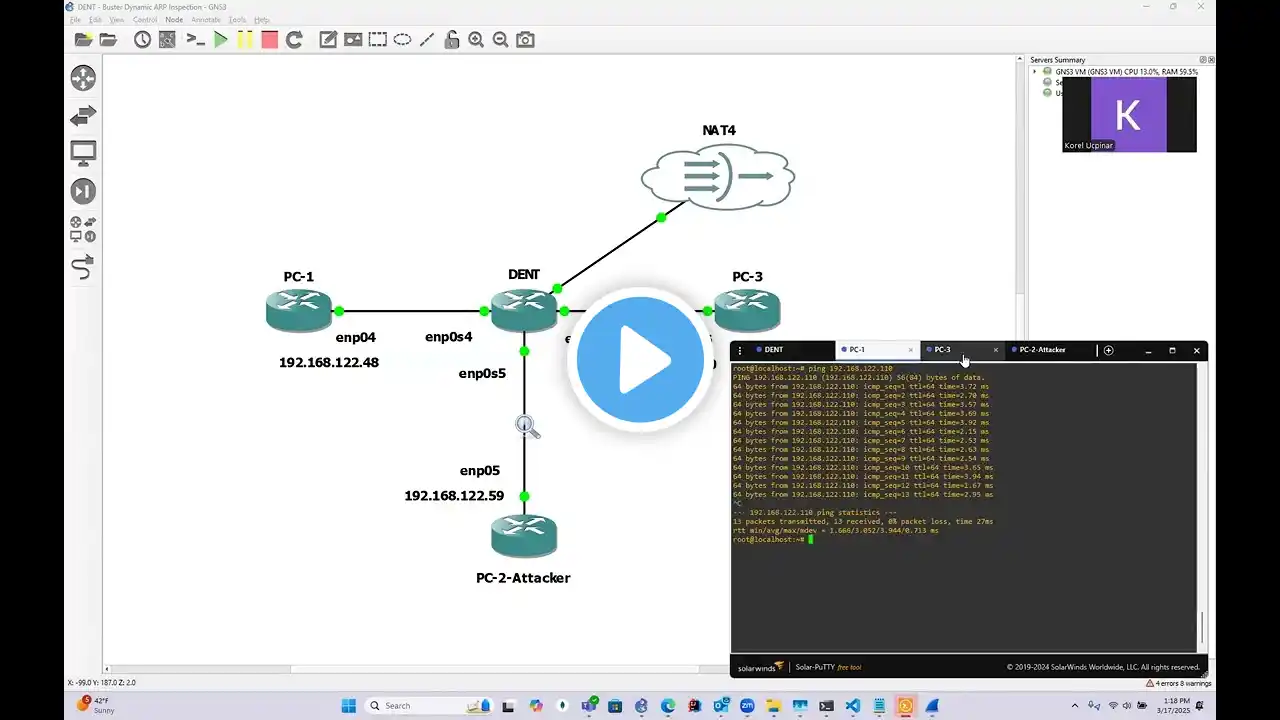
Initially, PC-1 and PC-3 communicate directly through the DENT switch. When PC-2 (the attacker) starts sending gratuitous ARP replies to both PC-1 and PC-3, it poisons their ARP caches. As a result, traffic intended for each device is instead forwarded to PC-2. The attacker then relays the intercepted traffic between PC-1 and PC-3, enabling a man-in-the-middle attack.